With the introduction of innovation in technology, a range of security layers rightly get integrated in IT Systems. As conventional security systems cannot address today’s dangerous threat landscape alone – introduction of network forensics and big data analytics is made to capture, process and analyze any security loophole. Furthermore, experts believe that Identity and Access […]
Information security starts by controlling – ‘Who’ has ‘What’ access to systems & data and ‘How’ that information is being accessed. Keeping in perspective the security aspect of information routed via SSH Key management, there are a few important questions for IT department heads to ponder over: Enterprises have been using SSH to access IT Systems. However, […]
Hybrid IT is the talk of the town – Cloud and On-Premises are coexisting and are being monitored, managed and utilized parallelly. The market is moving towards an era where technical transformation will be driven through a Hybrid approach. To harness this transformation, enterprises are required to manage multiple applications and identities that spans across on-premises […]
And how to fix that… Lack of control over SSH Keys is making hackers surpass Secure Shell security layer. The SSH Trick is when hackers use SSH Keys to log into servers. Most organizations are inadequately prepared for detecting a misuse of SSH keys. The trick is predominant, I realized this when I came across […]
I will pick up from the point where I left – Is Hybrid a problem or an opportunity?The takeaway for me – Hybrid IT will continue to be there for at-least next few years until we have standards, best practices and lessons learnt. For sure, managing Hybrid Eco-System is a challenge! I am assuming that most […]
Technology is a disruptive game, we discover something new with each passing minute. Businesses are out in the race, they are ready to embrace technology to be closer to business goals, automation and achieve competitive advantage. However, this cannot ignore the security climate associated with new technologies. It is, therefore, important to study and visualize […]
Deploying IAM Managed Services have become a norm for enterprises to track and secure their business information, be it about their finances or employees and their identities. Being a business owner, your client needn’t bother about slogging stats and security features threatening to wreak havoc to their enterprise. IAM Managed Services are not child’s play, so business […]
Growing concerns of cybersecurity have left business owners in dilemma. 80% of organizations prioritize their privilege security and expressed how critical it is to maintain an isolated environment to ensure IT security. Protecting privileged assets and isolating environments within your IT security eco-system is still a tough task. Because, cyber attacks may occur anytime and ruin […]
Irrespective of the industry you are catering to, Virtual Private Networks (VPN) are still used at large to meet the organizational IT ecosystem demands. These VPNs enable remote users to securely establish connection with the core IT infrastructure components, be it over on-prem setups or cloud infrastructure hosted with AWS or any other cloud provider. […]
As the world struggles to contain the current coronavirus onslaught, cybercriminals are implementing creative social engineering methods for accessing networks, systems, and passwords. Capitalizing on the fear and uncertainty of the situation, cybercriminals are exploiting a human weakness to tempt users into conducting insecure online behavior, leading to detrimental consequences in the present scenario. Cybercriminals […]
The key to the management of identities, an agile Active Directory (AD) acts as a map between names and values. In comparison to native tools, it is easier and faster for addressing the auditing and security needs of an enterprise, along with ensuring workflow streamlining, providing business continuity and optimizing IT capabilities. In fact, the […]
Jack owns a small and ambitious startup project. He deals with a stride of potential clients through his tiny army of professionals. Being at work on the go is what make Jack’s setup cast success. Competition is tough out there. Jack was never amused to notice that most of the target clients get poached by […]
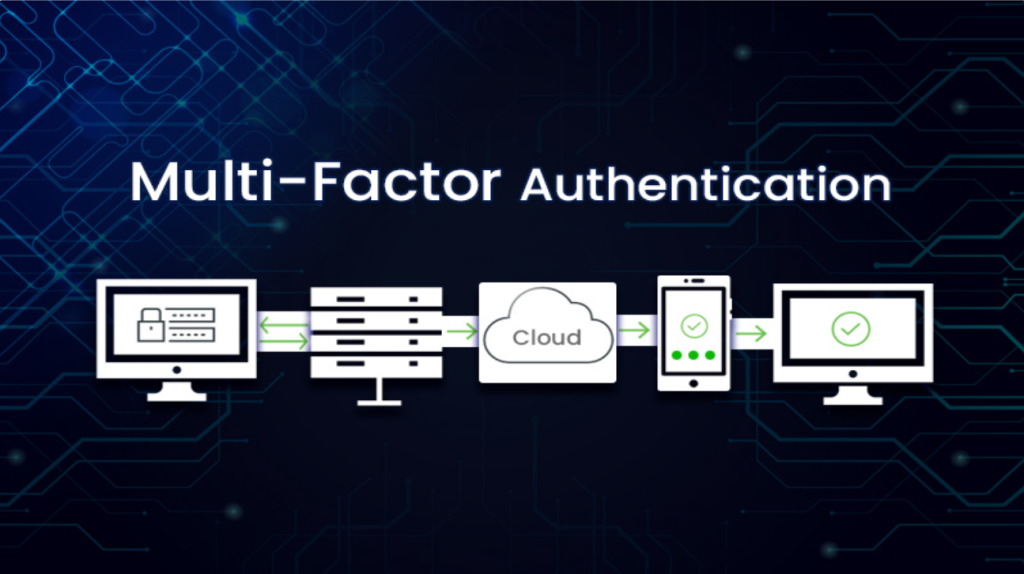
While making a shopping online on Amazon Indian portal – I was to login and follow through Two Factor Authentication (TFA) process. In the USA, TFA is widely adopted by financial organization or online banking, but when it comes to making purchases online – we are still stuck with static password type of authentication that […]
The always in fashion technical crime (hacking) runs on the idea of guessing or stealing a password. Passwords are a tiny piece of the puzzle that protects user identity. They are the keys that unlock access to various applications over the internet. These applications could be sensitive in nature depending on the quality of conversation […]
The parade of regulations related to cyber security means more compliance, discipline and agility to be showcased by businesses. Identity and Access Management technology has been instrumental in helping businesses achieve an upper hand on the regulatory requirements. Ever since the internet made a foray the government has been on the front foot to monitor activities over […]
Maintaining an organizations security is vital to its existence and development. In today’s age of globalization, businesses become increasingly collaborative and resources are availed of by a rising number of users. Therefore, organizations face complex challenges of maintaining their security as managing identities, authorizing and authenticating users to access sensitive enterprise resources becomes difficult and […]
Does anyone truly have Privacy? With Google tracking your interests, Facebook scanning each Photograph, Foursquare locating you every now and then, and apps like FindMyIphone, this becomes a very trivial question. In recent times, it has become crucial for users to draw a line between their online and offline lives. The picture is a matrix of regulations, […]
The cost of implementing an IAM solution is often frowned at, while organizations continue with struggle of managing identities, authorizing and authenticating users. We at Avancer strongly believe that this year is going to be a game changer, we are likely to witness a mind-set change where decision makers will view expenses in IAM as […]